Crack Wpa Handshake Online
The first thing you’ll need to do is obtain the network traffic for the WPA-Enterprise MS-CHAPv2 handshake you’d like to crack. For WPA2 Enterprise wireless handshakes, simply use a tool like hostapd-wpe in order to obtain ‘challenge’ and ‘response’ parameters. CrackStation uses massive pre-computed lookup tables to crack password hashes. These tables store a mapping between the hash of a password, and the correct password for that hash. The hash values are indexed so that it is possible to quickly search the database for a given hash. Look at that, 4 packets. That is the 4 way handshake we are looking for. So let’s dig into the packet a bit and see what’s in here. Click on the arrow beside 802.1X Authentication and this should give us the WPA Key. Marvelous, just one more thing to do now is to try and crack the key to get a password from it.
If you are planning to pentest a WPA/WPA2 network (with No WPS), I have two words for you: Good. Luck.
In all my experiments with penetration testing, I have found dictionary attacks on WPA/WPA2 handshakes to be the most annoying and futile exercises. This is because:
- going through each word in a dictionary file containing millions of words is time-consuming.
- success is not guaranteed (the passphrase may not be present in your dictionary).

During my experiments in India, the WiFi passphrases are usually a combination of Hindi and English words or a Hindu name which are, of course, not present in any dictionary that I download no matter how exhaustive it promises to be.
If you are still brave enough to try a dictionary attack on WPA handshake, here’s the procedure.
UPDATE: I have also posted a video on how capture and crack a WPA hanshake on my YouTube channel.
How to launch a Dictionary Attack on WPA Handshake
You might get lucky and your nearest WiFi password may be based on a common dictionary word or number sequence. In such a case, you may succeed with a dictionary attack.
Step 1: Enable monitor mode on wireless interface
This will start the monitor mode.
Step 2: Take note of the nearest WiFi networks.
Step 3: Take note of the channel of your target network, dump packets from that channel and save them to a local capture file.
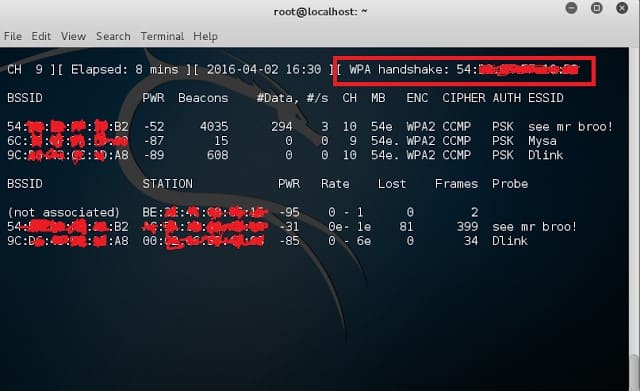
Step 4: Wait for WPA handshake capture
Crack Wpa Handshake Online Games
At this point, you can use ‘aireplay-ng’ to de-authenticate an associated legitimate client from the network. The point is that as he/she will authenticate again shortly, we will capture the handshake without having to wait too long:
If you don’t know the MAC of any associated client, simply ‘broadcast’ a ‘deauth’ to all clients:
Step 5: After you grab a WPA handshake comes the hard part of brute forcing using a dictionary. Use ‘aircrack-ng’ for this:
Now say your prayers and hope the passphrase is present in the dictionary you chose.
You can also use online distributed WPA/WPA2 handshake cracking tool on this website:
Crack Wpa Handshake online, free
Note that if the Access Point has WPS Enabled, it becomes easier to recover the WPA / WPA2 passphrase as there are only 11,000 possible combinations needed to brute force the WPS PIN due to an implementation flaw.
Disclaimer: This is for experimentation or authorized penetration testing purposes only.